Infection chains
To help webmasters find and remove malicious code faster, Yandex shows the host chains through which malicious code is loaded to the user's browser when the user views the infected pages.
This information helps to determine which block on the page loads malicious code.
For example, if the chain is:
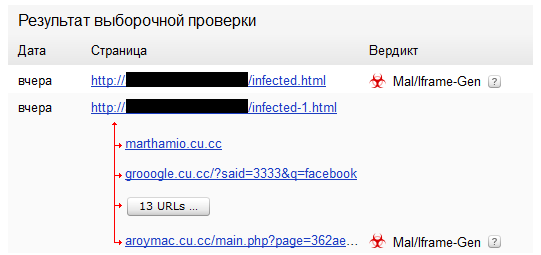
You should take one of these actions to stop the website from spreading malicious code:
Delete part of the web server page or the script that adds the
<script>or<iframe>tag to theinfected-2.htmpage. The tag loads the block frommarthamio.cu.ccor redirects to the site.Ask the owners of marthamio.cu.cc to fix their website so that it doesn't issue blocks that load other blocks from
groogle.cu.cc/?said=3333&q=facebook.Stop the spreading of malicious code from the
aroymac.cu.cc/main.php?page=362ae50582a6bb40resource.
Web server malicious code that writes a tag loading the block with marthamio.cu.cc or a redirect to it, can be obfuscated:
Intentionally made incomprehensible or unreadable. Look for the script parts that weren't written by you, especially the ones that have no structure and indentations.
Encoded. Such elements contain lines of meaningless characters and use the
eval, base64_decode, gzuncompress, gzinflate, ob_start, str_rot13, assert, create_function, preg_replacefunctions.Hidden as a
.htaccessstructure and other configuration files of the web server, scripting language interpreter, templates, and CMS settings.Dynamically loaded from a third-party web server (PHP functions
file_get_contents, curl_exec, and so on).
The web server malicious code may reappear after removal due to:
The web server backdoor.
Compromised web server passwords (FTP, SSH), hosting or CMS administrator panel.
Hacking the server by changing the root password or adding users with the necessary rights.
A backdoor or a bot on the webmaster's computer that allows to manage web server remotely and change the pages on behalf of the webmaster.
Web browser malicious code can be obfuscated with similar methods. It can use the eval, document.write, document.location, document.URL, window.location, and window.navigate structures, overridden "src" DOM elements, objects loaded with the <object> or <embed> tags, ActiveX, or changes in the page code made by downloaded objects. Also watch for long scripts and unnecessary string operations, such as reassigning or merging multiple lines into one.